
We Built a Solution to Gen Z's Loneliness Crisis at a Hackathon
Two-thirds of college students feel lonely. At Duke's AI Hackathon, we built Sync AI to change that.

Two-thirds of college students feel lonely. At Duke's AI Hackathon, we built Sync AI to change that.

You log into Canvas, your email, and your university portal every day without thinking twice. But the security protecting those logins? It's nowhere near as sophisticated as it should be. So my team and I decided to modernize it.
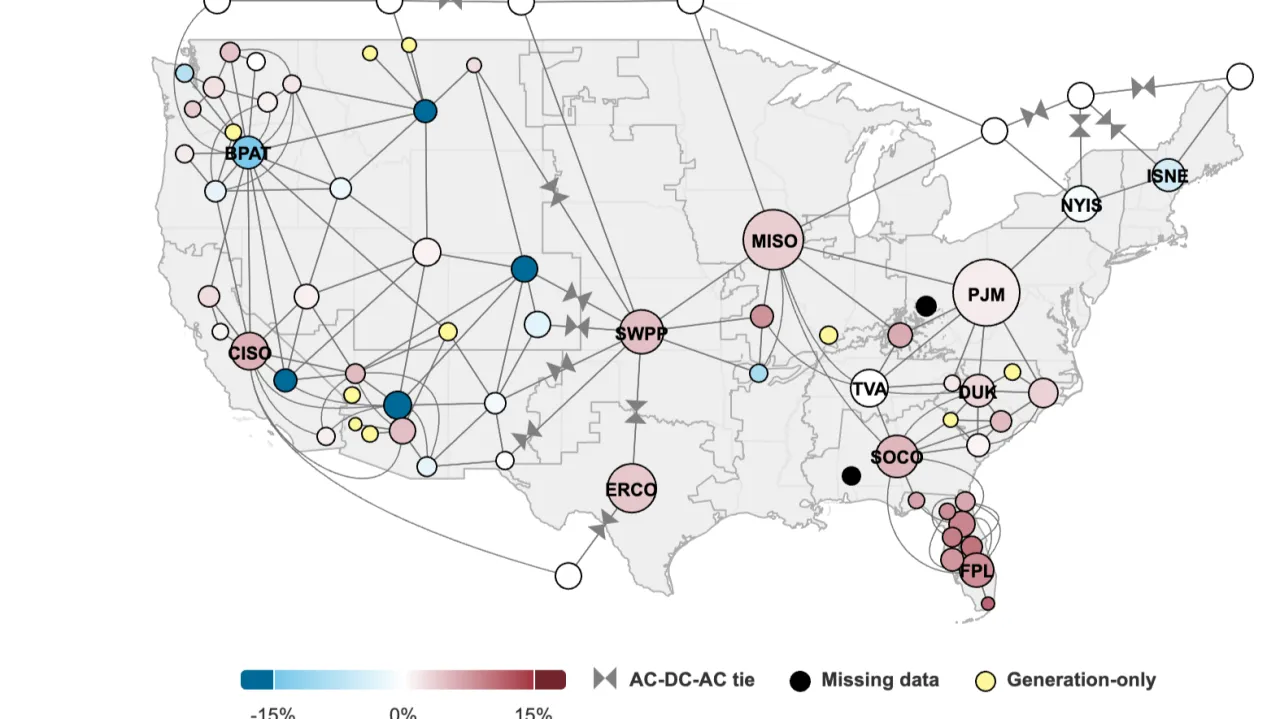
A data storytelling project exploring whether America's growing network of data centers is truly straining the power grid, or if the story in the numbers points to something more complex.

I have a preference for self-hosting my own applications. The biggest downside? Downtime during updates and reboots. Here's how I load balanced my entire stack to keep things running, even with a full server failing.

I am honored to have been recognized for academic and leadership excellence at the 2025 Paul and Virginia Engler College of Business Symposium with multiple honors and awards.